Let us know how we can help
Sales & Pricing
Speak to a rep about your business needs
Help & Support
See our product support options
General inquiries and locations
Contact usBMC AMI Security Session Monitor enables security and compliance teams to easily capture start-to-finish mainframe user behavior in real time, including all successful logins, session keyboard commands and menu selections, and specific data viewed without making any changes to mainframe applications.
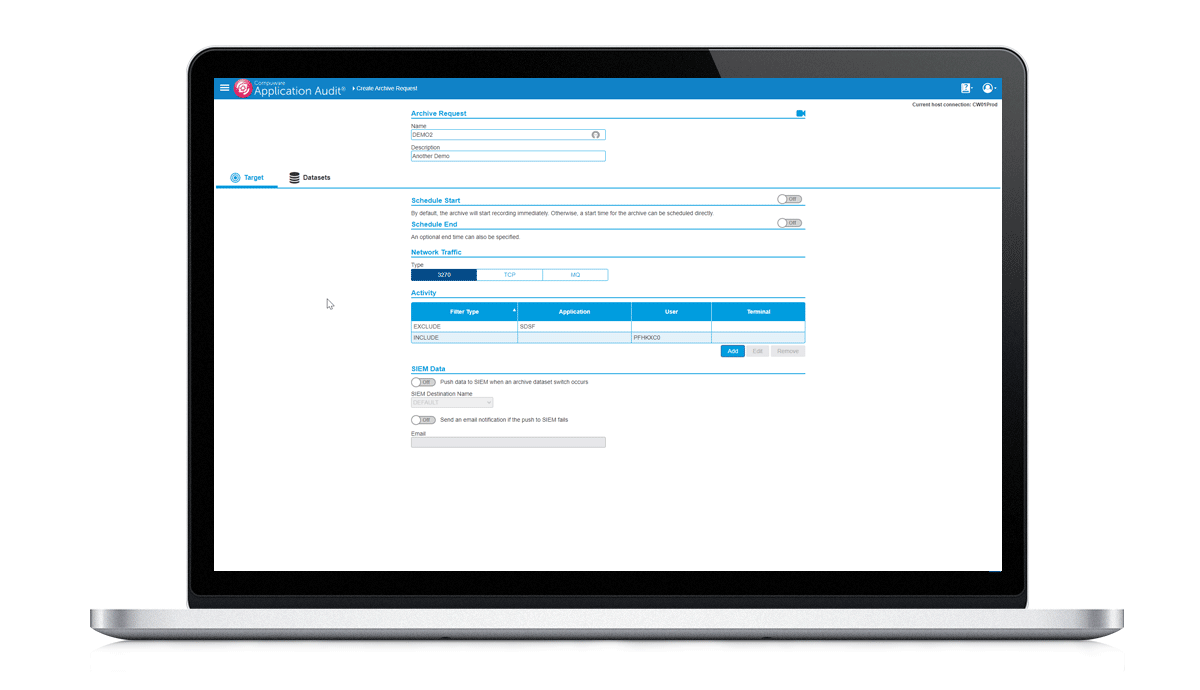
Strengthen security and compliance with rich user behavior intelligence
Application Audit enables enterprises to capture all relevant data about user access and behavior on the mainframe to mitigate cybersecurity risks and fulfill compliance mandates. Using Application Audit, security staff can:
-
Deter insider threats by capturing and analyzing start-to-finish user session activity
-
Integrate user behavior intelligence with popular SIEM engines to analyze the overall application environment
-
Support criminal/legal investigations with complete and credible forensics
-
Fulfill compliance mandates regarding protection of sensitive data
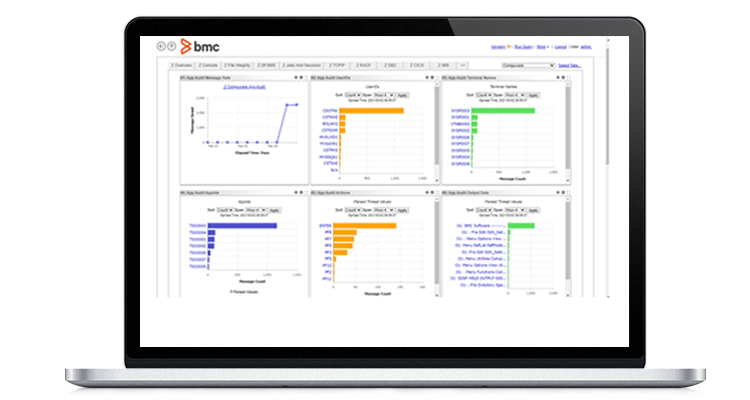
Discover internal threats and prevent future data breaches
-
Get deep insight into user behavior including data viewed, by whom, and which applications were used to access it
-
Leverage SIEM integrations for mainframe application-level insight to identify and reduce cybersecurity threats
-
Deliver the granular intelligence and reporting needed to comply with regulations such as HIPAA, GDPR, the Australian NDB scheme, as well as company security policies
-
Separate the system administrator’s duties from the responsibilities of auditors with a web UI, so that no single person is in a position to engage in malicious activities without detection
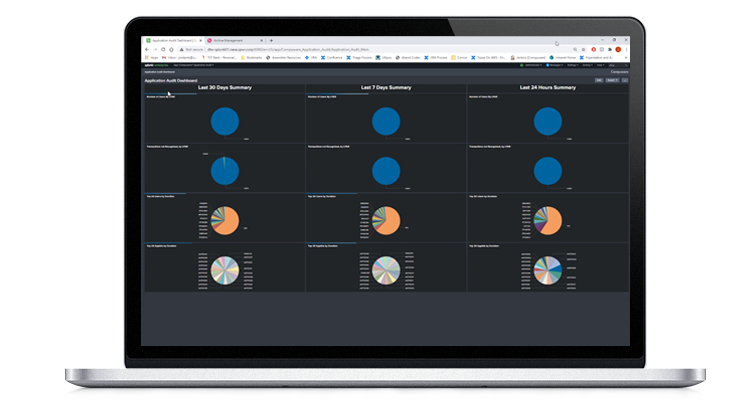
Empower security personnel with little mainframe experience
Application Audit reduces your dependency on specialized mainframe knowledge. Security personnel with no mainframe experience can set session recording parameters, enable the data to be delivered to SIEM systems, and review recording activities.
-
Automatically deliver Application Audit data to SIEM engines such as Splunk, Elasticsearch, IBM® QRadar® and HPE ArcSight ESM directly or in combination with BMC AMI Defender for z/OS or Precisely Ironstream®
-
Use the out-of-the-box Splunk-based dashboard to view behavior including users by LPAR; users by session duration; users with invalid transactions and more
Stu Henderson, Founder and President of the Henderson Group